As the UK’s Cyber Security and Resilience Bill (CSR Bill) is being discussed in the British Parliament, key changes the law will introduce in a bid to strengthen national security have been revealed.
This legislation comes at a critical time for the UK, with the National Cyber Security Centre (NCSC) reporting a 130% increase of "nationally significant" cyber incidents in 2025 compared to 2024 data.
Shona Lester, head of CSR Bill Team at the UK Department for Science, Industry and Trade (DSIT), recently spoke in detail about the proposed law at the Cybersecurity Business Network’s inaugural Parliament & Cyber Conference, held in Westminster, in London on November 24.
She said the bill will address some of the insufficiencies in “the UK's only cross-sector cyber security regulation,” the NIS directive.
UK Loses £15bn Every Year to Cyber-Attacks
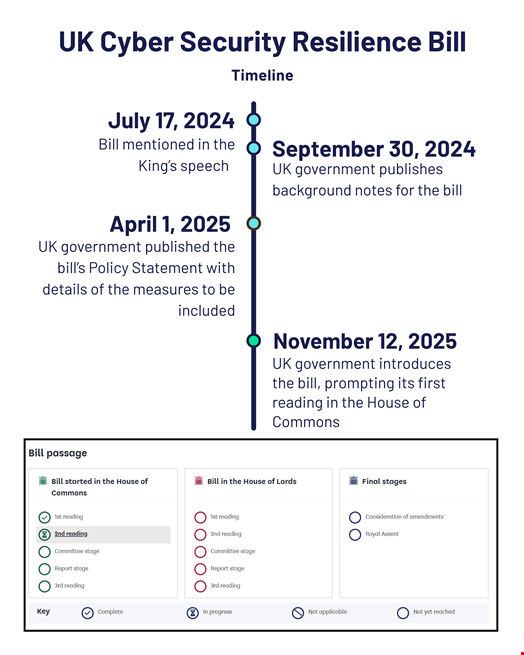
First mentioned in the King’s speech in July 2024, the bill was introduced to the House of Commons by the UK government on November 12.
While it is seen as the UK’s response to the EU’s NIS2 directive, as both build on the 2018 NIS directive, Lester emphasized that the CSR Bill’s main objective was “to make the UK a safer and more attractive place for business investment.”
She highlighted that, in a country where 96% of adults have a smartphone and 99% of businesses with 10 or more employees handle digitized data, the government is seeing a rapidly worsening threat picture.
“Our public services, our infrastructure and our economy at large are targets of attacks time and time again, from our hospitals, our universities, our local authorities to retailers, democratic institutions and government departments themselves,” she added.
A 2025 study by KPMG found that nearly £15bn is being lost from the UK economy every year as a result of cyber-attacks.
Cyber Security and Resilience Bill Explained
Lester said the CSR Bill will focus on protecting essential services, such as the National Health Service (NHS), transport and energy networks.
At the Parliament & Cyber Conference, she outlined some of the provisions that should be included in the law barring major changes during the parliamentary reading process.
Expanded Regulatory Scope
The requirements included in the bill will apply to four types of organizations, which will be considered as operators of essential services (OES):
- Data centers, which have been recognized as critical national infrastructure (CNI) entities since September 2024
- Large load controllers, which is the government’s term to refer to organizations managing smart appliances, such as supporting electric vehicle charging during peak times
- Managed service providers (MSPs), such as IT help desk and cybersecurity service providers. These will be regulated for the first time, bringing an additional 900-1100 firms into the scope of the law
- Other organizations that will be designated “critical suppliers” by UK regulators
The designated OES will need to meet “proportionate and up-to-date security requirements” drawn from the NCSC Cyber Assessment Framework (CAF), Lester said.
Enhanced Incident Reporting
The CSR Bill will update the current incident reporting regime to cover a wide range of incidents about the potential to cause significant disruption, such as pre-positioning attacks.
“Right now, the regulators and the NCSC only get informed about cyber incidents if they caused significant disruption – and this is just simply too late to mitigate the attacks in many cases,” Lester added.
Under the CSR Bill, OES will be required to:
- Notify regulators within 24 hours of becoming aware of an incident. Reports suggested the bill could also require OES to send a full report to relevant authorities within 72 hours
- Inform customers if they are likely to be impacted by a cyber incident
- Report potential incidents that could cause significant disruption, not just those that have already caused damage
“The bill will also provide greater clarity on information sharing with provisions to ensure information can be shared at scale when appropriate,” Lester promised.
Strengthened Regulatory Powers
The bill will amend the existing regulatory powers and enforcement mechanisms.
First, the Secretary of State will be able to set common objectives for the 12 different regulators, which will each be allowed to take direct targeted action in response to significant national security threats, she explained.
Additionally, it was previously reported that the powers of the Information Commissioner’s Office (ICO) will also be enhanced, enabling it to identify the most critical digital service providers and adopt a proactive approach to assessing cyber risk.
Lester mentioned some enhancements in enforcement mechanisms and the sanction regime, including:
- Simplified penalty bands
- Amended maximum fines to enable higher penalties for non-compliance – previous reporting suggested potential turnover-based penalties
Finally, Lester suggested that, once adopted, the CSR Bill could quickly be updated with second legislation, with possible additions, such as bringing more sectors into scope, updating security requirements, adding third-party risk requirements.
Expert Reactions to the CSR Bill
Many of the those speaking during the Parliament & Cyber Conference noted that the scope of the CSR Bill remained “very narrow” and expressed wishes to see either a broader scope or more stringent security requirements for covered entities.
Shaukat Ali-Khan, Chief Digital Information Officer for the NHS in West Yorkshire, said he hopes the bill will improve clarity on security requirements’ implementation mechanisms and requested a separate mechanism for education across OES, the public sector and the general public.
Emma Philpott, CEO of the IASME Consortium, the NCSC's Cyber Essentials Partner, said she hopes for ways to ensure businesses take basic cybersecurity measures and urged to implement mechanisms to secure organizations beyond just those currently covered by the bill.
She also said she was in favor of enforcing regulations which push companies to implement security through supply chain requirements.
Chris Francis, director of government relations at SAP, said he expects “a thorough regulatory impact assessment” and would like to see “mandatory consultation with businesses on secondary legislation.”
Finally, Ali-Kha, Francis and Jen Ellis, a fellow at the Royal United Services Institute (RUSI), emphasized the need to align the CSR Bill with other legislations and best practices from the EU (including the Cyber Resilience Act), the US, and other members of the Organization for Economic Co-operation and Development (OECD).
As Lester was delivering her speech during the conference, the House of Commons Business and Trade Committee published a new report calling for the UK government to enshrine in law a new approach to economic security, citing a growing menace to the country from cyber and other threats.
